-
Masks all input fields, except for those with the CSS class
adora-unmask. -
Masks all HTML elements with the CSS class
adora-mask. -
Blocks all HTML elements with the CSS class
adora-block. - Captures data only on pages where the snippet is installed, or where the URL is explicitly allowlisted. It also respects URL blocklists.
What does Adora capture?
When an end user’s browser loads with the Adora JavaScript snippet enabled, Adora begins capturing the HTML and CSS of the page. For example, consider the following page:Key privacy controls
Masking
Masking replaces text content with * characters, allowing text structure to remain visible while obscuring specific values. For example: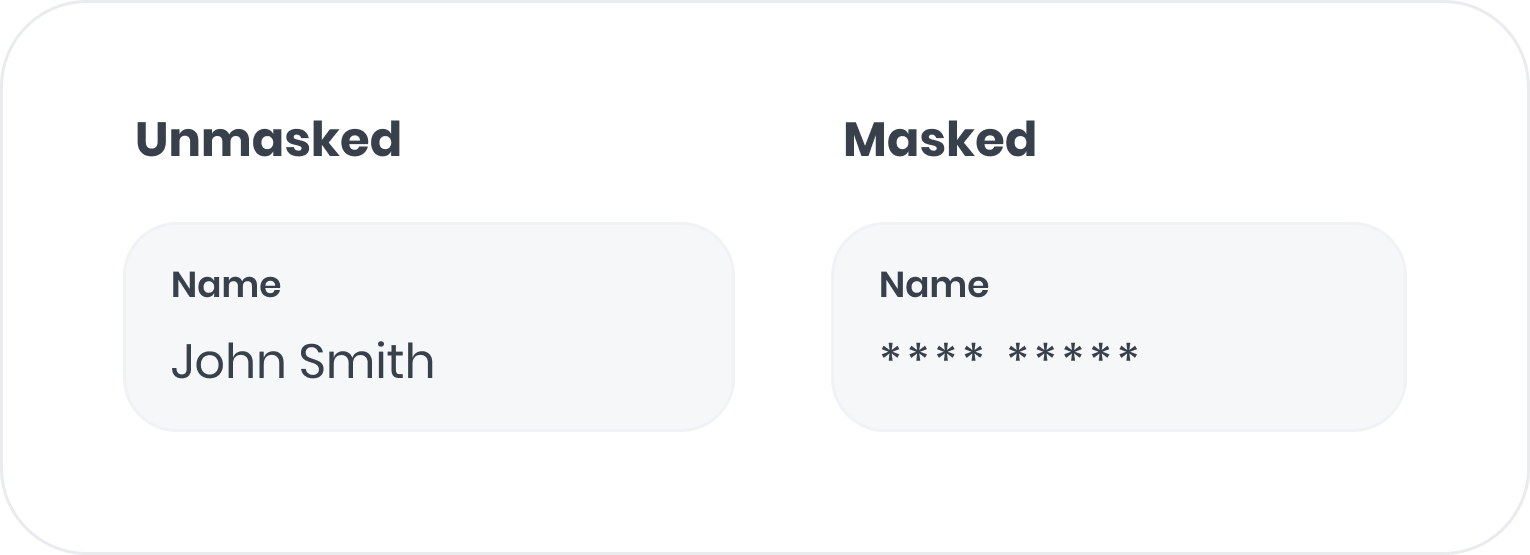
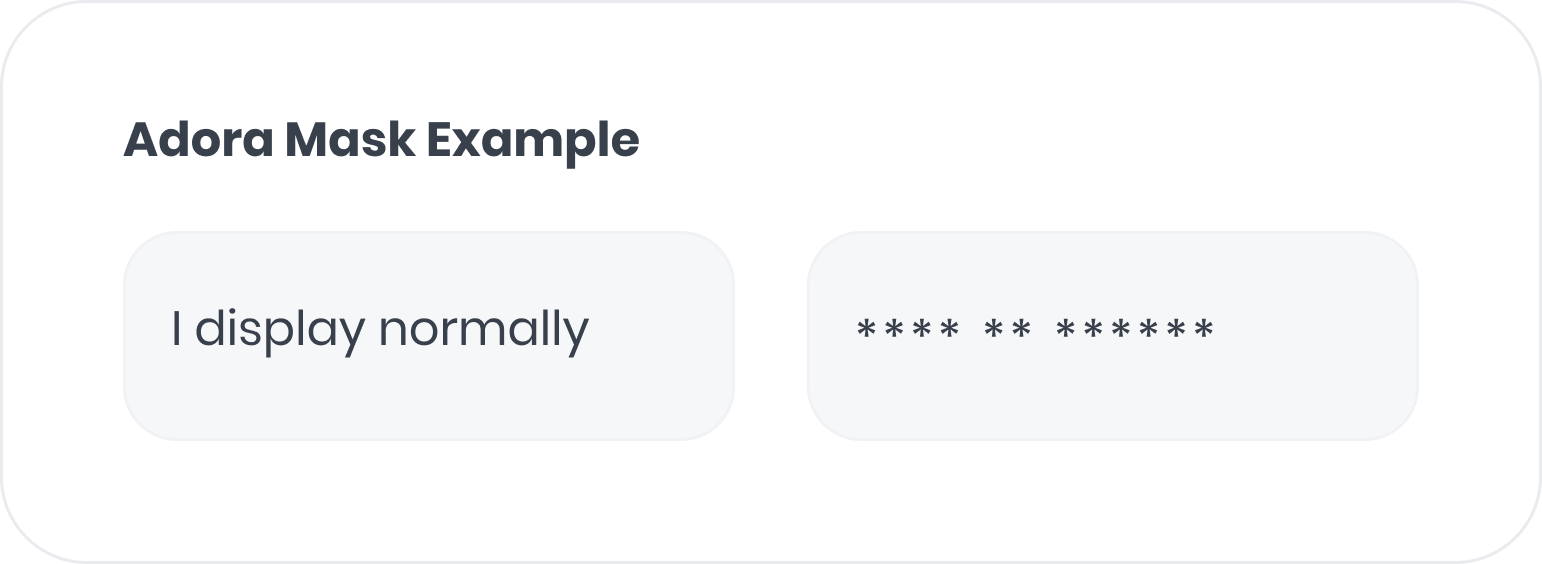
CSS class masking
To mask an element, add theadora-mask CSS class to the HTML element. For example:
Data attribute masking
To mask an element, adddata-adora-mask="true" to the HTML element. For example:
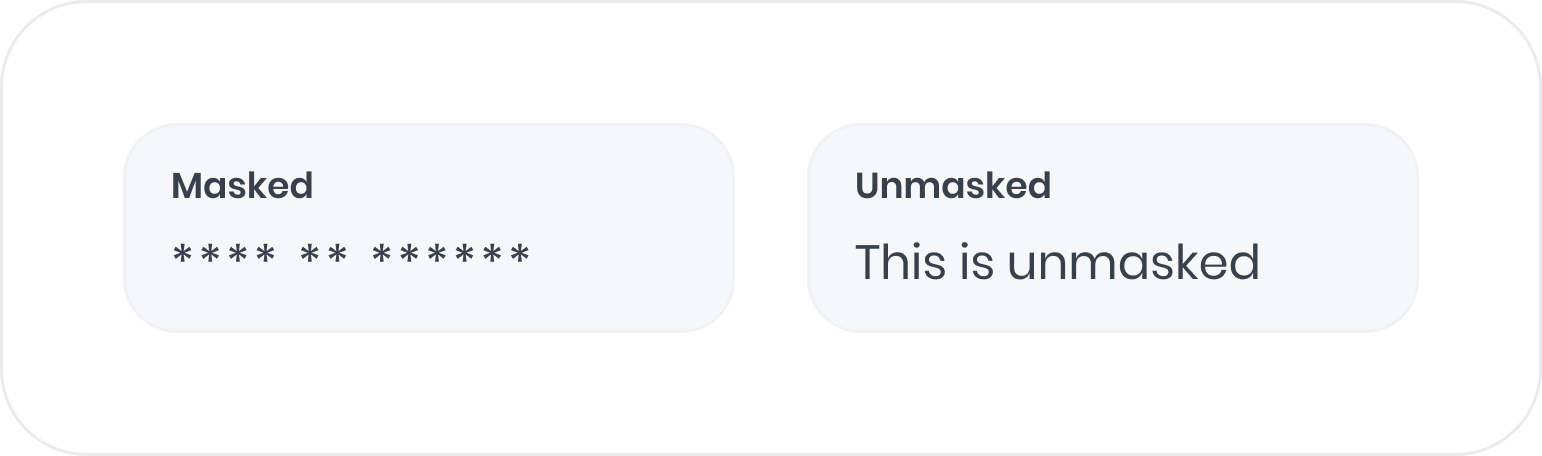
Unmasking
Unmasking allows you to see user input, which can be helpful for support request fields or search boxes. Apply theadora-unmask CSS class to unmask input fields. For example:
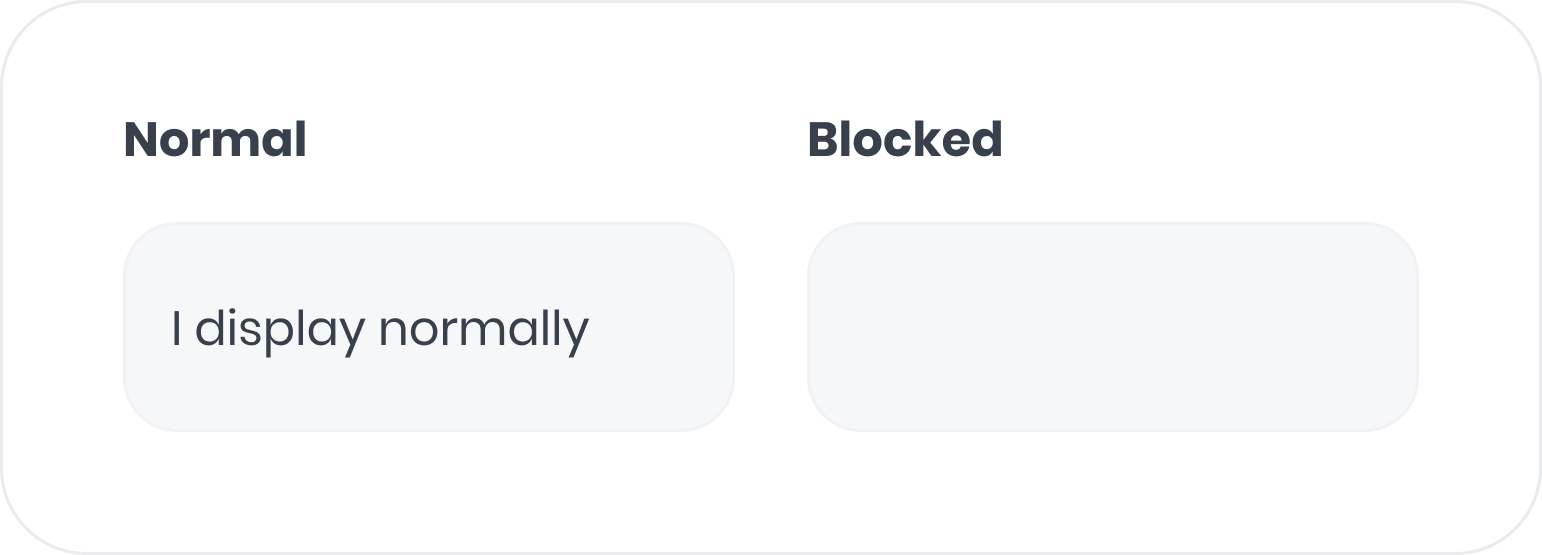
Blocking
Blocking replaces content with an empty transparent box while preserving the original spacing. This is useful for removing entire images or sections from being captured. There are two ways to block, using a CSS class or a data-attribute.CSS class blocking
Add theadora-block CSS class to an element to block its content.
For example:
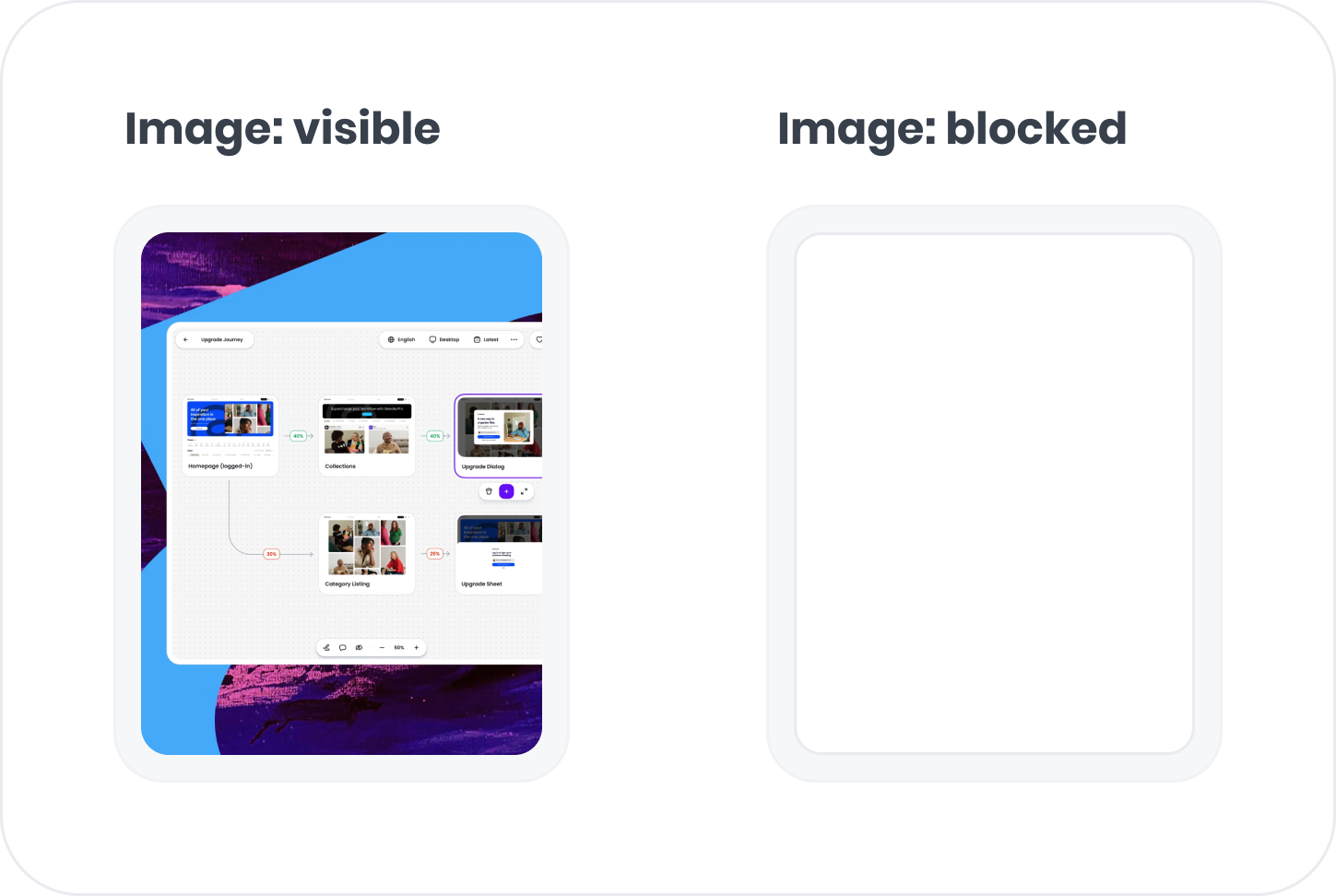
Data attribute blocking
Add thedata-adora-block attribute to an element to block its content.
For example:
URL Management
Adora offers both automatic and opt-in URL management for greater control of captured data. To manage URL controls for your organization, please visit the access control tab in settings here, or contact us.Controlling What URLs Adora Captures
By default, Adora captures all URLs where the snippet is installed. To prevent Adora from capturing specific URLs, you can:- Avoid adding the script to those pages (e.g., using rules in Google Tag Manager or your codebase).
- Install the snippet on all pages but configure a blocklist or allowlist for URLs. This is especially useful for single-page applications (SPAs) with dynamic routing, where managing snippet installation may be more complex.
/private-section/*blocks direct pages under private-section (like /private-section/page1)/private-section/**blocks all pages under private-section, including deeply nested ones (like /private-section/accounts/user/settings)
Redacting Path Data in URLs
URL aggregation is a key feature of Adora that simplifies your workflow by grouping similar paths. For example, URLs like/page/uuid1, /page/uuid2, and /page/uuid3 are aggregated into /page/* in the UI. By default, this aggregation occurs server-side, meaning the full path (e.g., /page/uuid1) is sent to Adora.
If sending full paths is not desirable—e.g., when paths include sensitive data like uuid1—you can define client-side grouping rules using regex patterns. These rules allow Adora to strip or group paths before they are sent to the server. For example, you could provide the rule /page/* to ensure all such URLs are captured as /page/*.
Query Parameters
By default, Adora removes all query parameters to minimize the risk of unintentionally capturing sensitive information, such as authentication tokens. This default behavior provides peace of mind out of the box. However, there are scenarios where query parameters are essential for differentiating steps within the same page. For example, a signup process might use/signup?step=1. By default, Adora would treat all such pages as /signup. To distinguish between steps, you can explicitly allow specific query parameters, such as step, to be captured.
Stopping and restarting capturing
You can stop (or pause) Adora from capturing events by callingwindow.adoraStop() anytime.
You can verify that Adora has been stopped capturing events by verifying that no requests being sent to /sessions/SESSION_ID/events in the “Network” tab.
The snippet will not capture any events until window.adoraStart() has been called again.